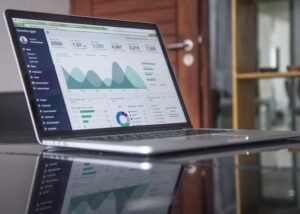
Cyber Attacks Have Led to Focus More on Data Security
The recent change in working pattern has led to Work from Home and since then it has been difficult for accountancy firms to keep a check on the data. Thus, it has been hard for firms and employees to deal with security. “That being said, the chief officer for Calligo, Adam Ryans has suggested that the change has been difficult and by default, the change